Trusted Communication Partner
![]()
IoT environments may contain all sorts of devices and other components that are not under your direct control. These may pose a security or privacy risk to your devices and data. Limit your devices’ autonomy and configure them to communicate only with trusted partners. Block and notify connection attempts from other sources.
Aliases:
Well-Known Target
Context:
In the IoT, devices may communicate with many other communication partners, such as backend servers, applications, or other devices. Some of these connections may be used regularly while others are used infrequently. Besides, the number of available communication partners may be constantly changing as new apps or services are created and devices change their location.
Problem:
In a dynamic environment there may be multiple potential communication partners available for a device. These may not be known or trusted and may pose a security risk as attackers may try to use them to get access to devices and their networks.
Forces:
-
Threats: Other components may pose a threat by trying to access the device or by launching a denial of service attack.
-
Uninvited Communication: Uninvited communication should be blocked where possible.
-
Functionality: The security measures should not impede normal operation and communication.
-
Flexibility: Some use cases are rather static and do not involve frequently changing communication partners. Others are the opposite and require interactions with frequently changing communication partners, which increases the risk of potential attacks.
Solution:
Configure the device with a single communication partner or a list of communication partners that you trust. Only allow incoming or outgoing communication with these Trusted Communication Partners. Block other communication attempts and notify the person responsible for investigating these attempts.
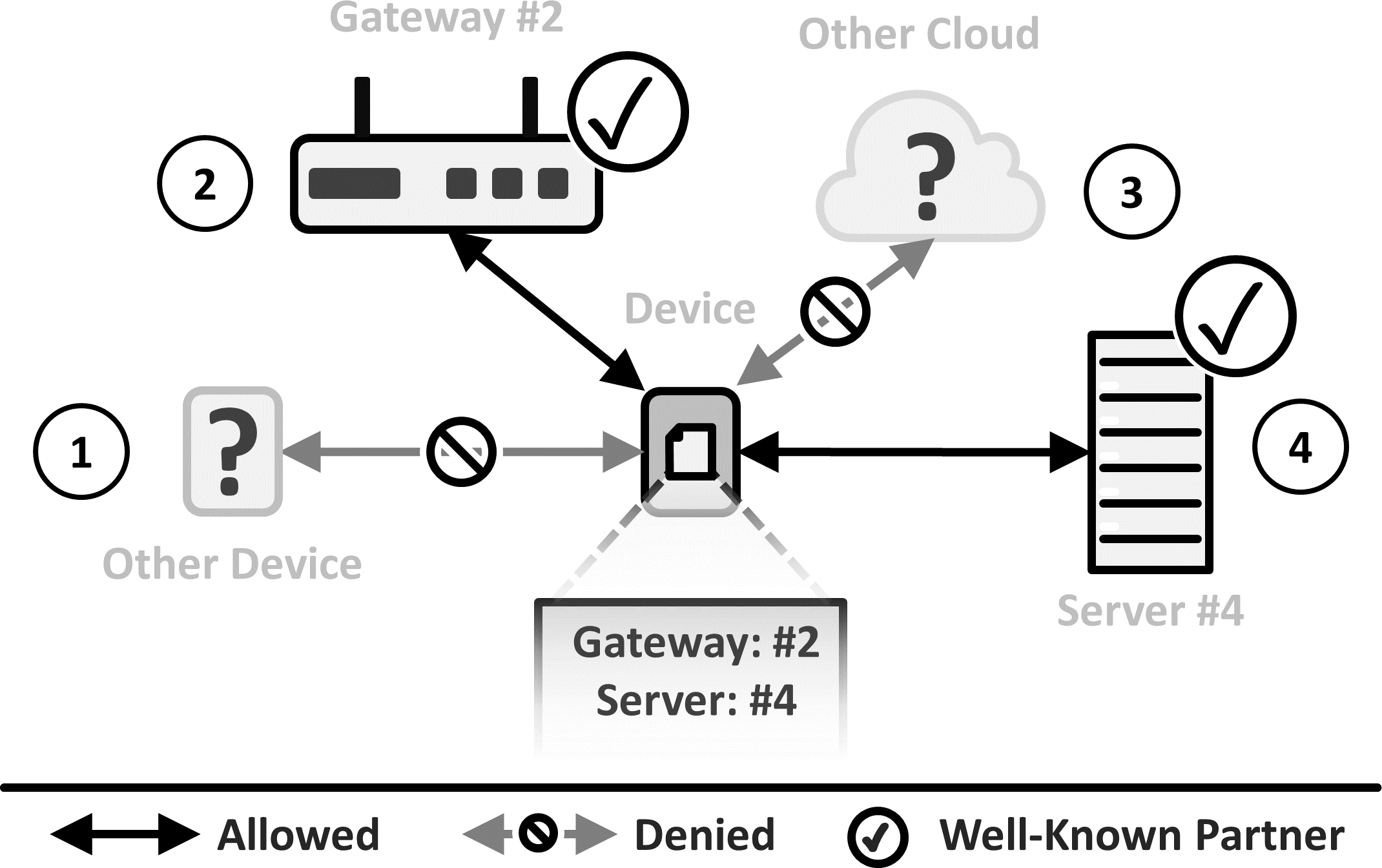
Solution Details:
Benefits:
Variants:
Related Patterns:
Known Uses:
- L. Reinfurt, U. Breitenbücher, M. Falkenthal, P. Fremantle, and F. Leymann, “Internet of Things Security Patterns,” in Proceedings of the 24th Conference on Pattern Languages of Programs (PLoP), 2017. Available at https://dl.acm.org/citation.cfm?id=3290305