Remote Lock and Wipe
![]()
You want to prevent attackers to gain access to your data or network when a device is lost or stolen. Add functionality to the device which allows you to remotely wipe the data on the device or lock some or all functionality.
Aliases:
Remote Factory Reset, Remote Locking, Remote Wiping
Context:
A device is connected to a backend server and is in danger of being lost or stolen. This might be the case because it is installed at an easily accessible public location, or a remote and unmonitored location. The device might have functionality that must not be accessed by a thief. It might also contain classified data that has to be kept protected. The data might or might not be encrypted. The device might be retrievable when it is lost or stolen, but it might also vanish forever.
Problem:
Some devices might be lost or stolen. You want to prevent attackers from misusing the functionality of the device, or from gaining access to the data on the device or to the network through the device.
Forces:
-
Long-term Data Security: If the device is irretrievably stolen, an attacker might have ample time to break encryptions if data on the device is encrypted.
-
Fine-grained Control: Depending on the situation, the type of device and the content on the device, different actions might be necessary in the case of loss or theft.
-
Reversibility: A lost or stolen device might eventually be returned, so any actions taken should be reversible if possible.
-
Remote Control: Since the device is no longer physically available, the activation of additional security mechanisms has to work remotely.
Solution:
Make the device a managed device that can receive and execute management operations from the backend server. Allow authorized users to use the backend server to trigger functionality on the device that can delete files, folders, applications or memory areas, revoke or remove permissions, keys, and certificates, or enable additional security feature. Execute triggered functions as soon as the device receives them and provide acknowledgment to the backend.
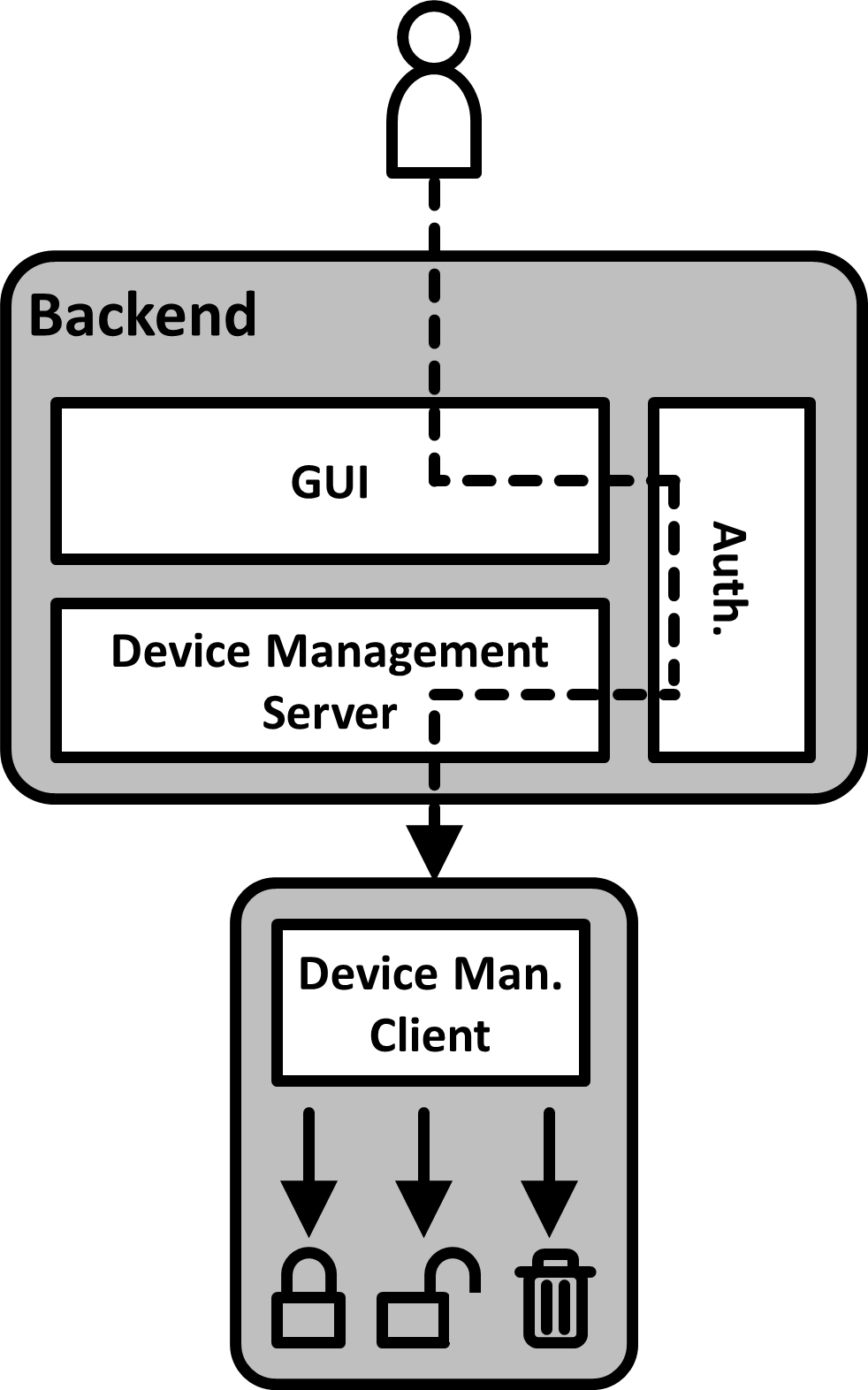
Solution Details:
Benefits:
Variants:
Related Patterns:
Known Uses:
- L. Reinfurt, U. Breitenbücher, M. Falkenthal, F. Leymann, and A. Riegg, “Internet of Things Patterns,” in Proceedings of the 21st European Conference on Pattern Languages of Programs (EuroPLoP), ACM, 2016. Available at http://dl.acm.org/citation.cfm?id=3011789