Personal Zone Hub
![]()
Managing the permissions, data sharing, and control of devices across multiple Device Gateways and clouds is complex. Create a Personal Zone Hub which handles such settings in a central place under the control of the device owner or a trusted third party. Allow owners to selectively provide access to their devices and data through this hub.
Context:
Devices, services, applications, and the data they produce usually have an owner, such as a person or an organization. Together, these components create the personal zone of their owner. This personal zone may contain all kinds of devices, applications, and data that may allow others to identify, track, or gain insights about the owner. Thus, the owner is usually interested in controlling and restricting access to his personal zone.
Problem:
Users have an increasing number of IoT devices. Managing the permissions, data sharing and control of these devices across multiple gateways and cloud systems is complex.
Forces:
-
Ownership: You own all the components and data in your personal zone and thus should be in charge when it comes to granting access to them.
-
Manageability: Handling access to the devices in your personal zone on a per device basis may be cumbersome. Each device may have a different mechanism for handling access.
-
Trust: The user may not trust third parties with the management of his devices, apps, software, and data.
-
Decentralization: Having only one party being responsible for matters of authorization may be a disadvantage. It would concentrate these capabilities in one place and allow this party to take advantage of its position. It may also lead to vendor lock-in.
Solution:
Create a Personal Zone Hub which unifies the management and control of all devices, services, apps, and data of one user into a single, trusted system. Make the hub permanently addressable. Allow the user to selectively share access to some or all the data and functionality encompassed by the zone.
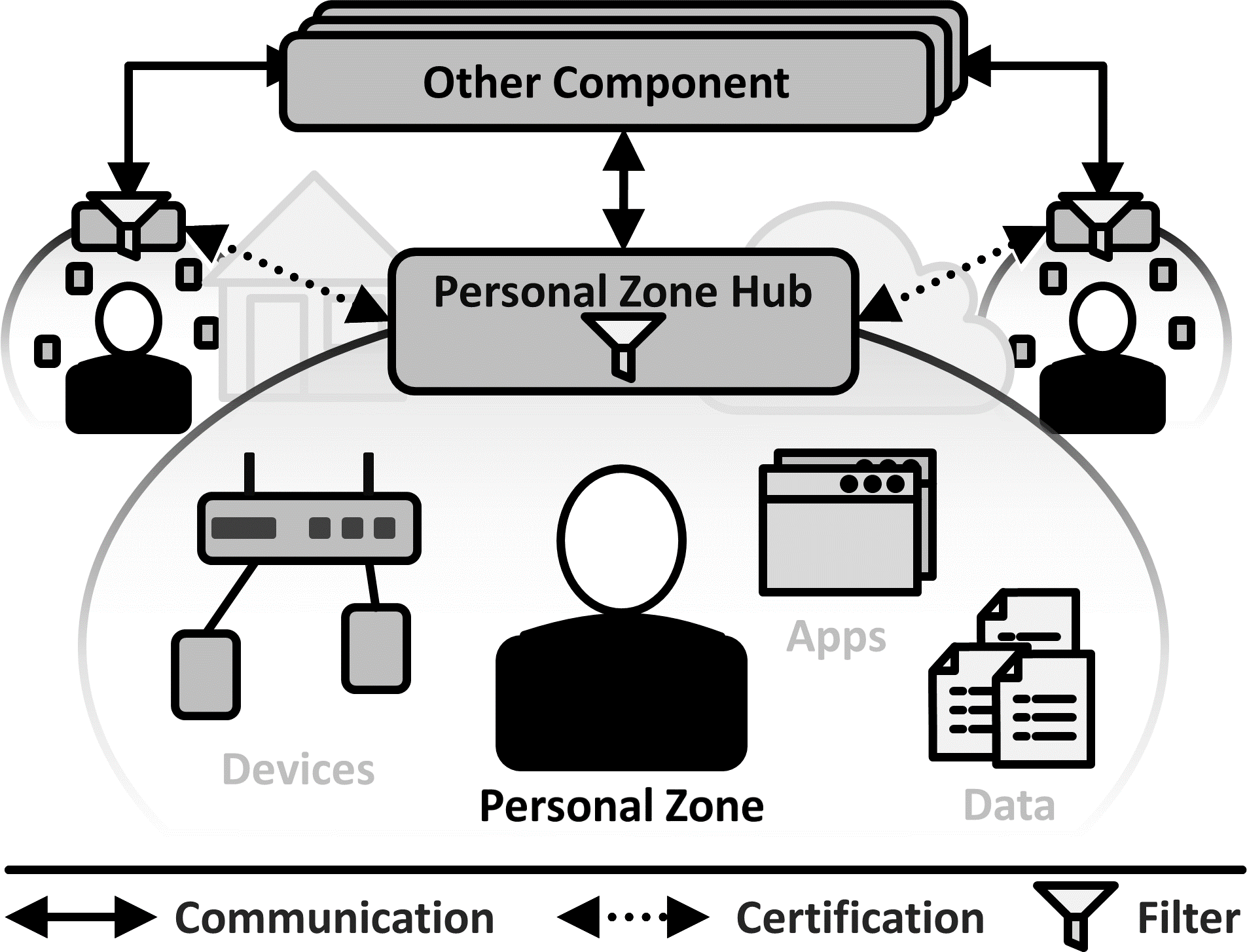
Solution Details:
Benefits:
Variants:
Related Patterns:
Known Uses:
- L. Reinfurt, U. Breitenbücher, M. Falkenthal, P. Fremantle, and F. Leymann, “Internet of Things Security Patterns,” in Proceedings of the 24th Conference on Pattern Languages of Programs (PLoP), 2017. Available at https://dl.acm.org/citation.cfm?id=3290305