Outbound-Only-Connection
![]()
Attackers may send unsolicited connection requests to devices to get them to connect to an infected communication partner. To prevent this, configure devices so that only they initiate connections. Block all incoming connection requests.
Context:
Devices and other components often have to communicate bidirectionally: Devices send data to other devices or services for monitoring, processing, analysis, or storage purposes. Devices also receive commands which control actuators attached to them or trigger functionality built into them. This communication poses a security risk as attackers might try to gain access to devices to manipulate them.
Problem:
Devices are a target for attackers who try to gain access to their network. They may send unsolicited communication requests to the devices to get them to connect to an infected communication partner or to misuse them.
Forces:
-
Security: Unsolicited request must be ignored.
-
Functionality: The original functionality of the devices has to stay intact. They have to be able to send their data and they also have to be able to receive commands from other communication partners.
-
Constraints: Many IoT devices are constrained in their capabilities. This limits the viability of more sophisticated solutions for controlling communication, such as Firewalls or Packet Filters [2].
Solution:
Program devices so that only they initiate connections. Deny all incoming communication requests that are not responses to a connection already created by the device.
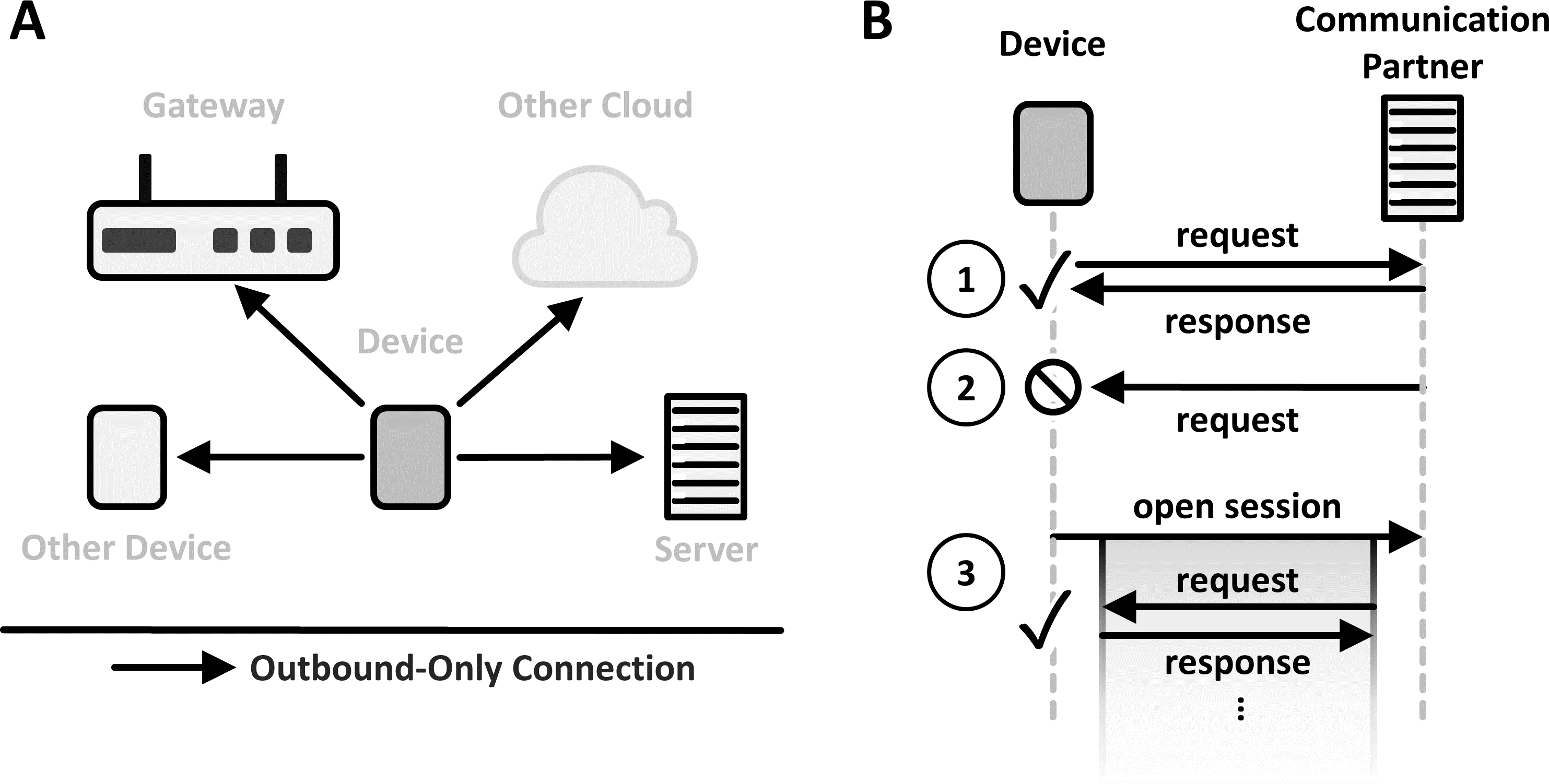
Solution Details:
Benefits:
Variants:
Related Patterns:
Known Uses:
- L. Reinfurt, U. Breitenbücher, M. Falkenthal, P. Fremantle, and F. Leymann, “Internet of Things Security Patterns,” in Proceedings of the 24th Conference on Pattern Languages of Programs (PLoP), 2017. Available at https://dl.acm.org/citation.cfm?id=3290305
- M. Schumacher, “Firewall Patterns,” in Proceedings of the 8th European Conference on Pattern Languages of Programms (EuroPLoP ’2003), 2003.